GenderMag Personas Foundations Document
GenderMag currently has three personas: Abi, Pat, and Tim. This document shows the foundations behind them.
Abi, Pat, and Tim are identical in several ways: all have the same job, live in the same place, and all are equally comfortable with mathematics and with the technology they regularly use. Their differences are strictly derived from the gender research on five facets: their Motivations to use software, Information Processing Styles, Computer Self-Efficacy, Attitudes toward Risk, and style of Learning new technologies. Tim's facet values are those most frequently seen in men, Abi's facet values are those frequently seen in women that are the most different from Tim's, and Pat's facet values add coverage of a large fraction of people different from both Abi and Tim.
Abi (Abigail/Abishek) Persona Foundations
Abi represents a fraction of people with backgrounds similar to theirs. For gender data on people similar to and different from Abi, see the Footnotes.
Note: All gray-background portions are fundamental to Abi. In contrast, the white-background portions can be customized to match your software's target audience.

- 28 years old
- Employed as an Accountant
- Lives in Cardiff, Wales
Abi has always liked music. On their way to work in the mornings, Abi listens to music that spans a wide variety of styles. But when Abi arrives at work, they turn it off, and begin their day by scanning all their emails first to get an overall picture a before answering any of them. (This extra pass takes time but seems worth it.) Some nights Abi exercises or stretches, and sometimes Abi likes to play computer puzzle games like Sudoku. [Sources: 7, 9, 18, 23, 25, 26, 29, 30, 31, 35, 37]
Background Knowledge and Skills
- Abi works as an accountant. They are comfortable with the technologies #dbdbdbthey use regularly, but they just moved to this employer 1 week ago, and their software systems are new to Abi b .
- Abi says they're a "numbers person", but they have never taken any computer programming or IT systems classes. Abi likes Math and knows how to think with numbers c . Abi writes and edits spreadsheet formulas in their work. [Sources: 40, 16, 33]
- In their free time, Abi also enjoys working with numbers and logic c . Abi especially likes working out puzzles and puzzle games, either on paper or on the computer. [Sources: 16, 33]
Motivations and Strategies
- Motivations d : Abi uses technologies to accomplish their tasks. Abi learns new technologies if and when they need to, but prefers to use methods they are already familiar and comfortable with, to keep their focus on the tasks they care about. [Sources: 5, 6, 10, 20, 21, 24, 28, 37]
- Information Processing Style e : Abi tends towards a comprehensive information processing style when they need to get more information. So, instead of acting upon the first option that seems promising, Abi gathers information comprehensively to try to form a complete understanding of the problem before trying to solve it. Thus, Abi's style is "burst-y"; first they read a lot, then they act on it in a batch of activity. [Sources: 7, 9, 18, 23, 25, 26, 29, 30, 31, 35, 37]
Attitude to Technology
Abi is generally comfortable using familiar technology, but they do not get a big kick out of obtaining the latest gadgets or learning how to use them f . Abi prefers to stay with the technologies for which they have already mastered the peculiarities [5, 28], because of the following facets:
- Computer Self-Efficacy g : Abi has low confidence about doing unfamiliar computing tasks. If problems arise with their technology, Abi often blames themself for these problems. This affects whether and how Abi will persevere with a task if technology problems have arisen. [Sources: 1, 2, 3, 4, 5, 6, 15, 17, 19, 22, 27, 28, 32, 34, 38]
- Attitude toward Risk h : Abi's life is a little complicated and they rarely have spare time. So Abi is risk averse about using unfamiliar technologies that they might need to spend extra time on, even if the new features might be relevant. Abi instead performs tasks using familiar features, because they're more predictable about what Abi will get from them and how much time they will take. [Sources: 10, 14, meta-analysis 12, survey 39]
- Learning: by Process vs. by Tinkering i : When learning new technology, Abi leans toward process-oriented learning, e.g., tutorials, step-by-step processes, wizards, online how-to videos, etc. Abi doesn't particularly like learning by tinkering with software (i.e., just trying out new features or commands to see what they do), but when Abi does tinker, it has positive effects on their understanding of the software. [Sources: 4, 5, 8, 11, 21, 24a, 36]
Pat (Patricia/Patrick) Persona Foundations
Pat represents a fraction of people with backgrounds similar to theirs. For gender data on people similar to and different from Pat, see the Footnotes.
Note: All gray-background portions are fundamental to Pat. In contrast, the white-background portions can be customized to match your software's target audience.

- 43 years old
- Employed as an Accountant
- Lives in Cardiff, Wales
Pat loves public transportation and knows at least three routes to get there from home. When they arrive at work, Pat scans all their emails first to get an overall picture a before answering any of them. (This extra pass takes time but seems worth it.) Some evenings Pat plays computer puzzle games like Sudoku before bed. [Sources: 7, 9, 18, 23, 25, 26, 29, 30, 31, 35, 37]
Background Knowledge and Skills
- Pat works as an accountant in a consulting firm. They prefer to stay with the technologies for which they have already mastered the peculiarities. Pat just moved to this employer 1 week ago, and their software systems are new to Pat b .
- Pat describes themself as a "numbers person" c , but they are not a professional programmer and have never taken any computer programming or IT systems classes. Pat has a degree in accounting so they know plenty of Math and know how to think in terms of numbers. [Sources: 40, 16, 33]
- Even though Pat's an accountant and deals with numbers all day at work, they like working with numbers c in their free time, too. Pat especially likes Sudoku and other computer games that involve puzzling. [Sources: 16, 33]
Motivations and Strategies
- Motivations d : Pat learns new technologies when they need to, but Pat doesn't spend their free time exploring technology or exploring obscure functionality of programs and devices that they use. Pat tends to use methods they are already familiar and comfortable with to achieve their goals. [Sources: 5, 6, 10, 20, 21, 24, 28, 37]
- Information Processing Style e : Pat leans towards a comprehensive information processing style when they need to gather information to problem-solve. So, instead of acting upon the first option that seems promising, Pat first gathers information comprehensively to try to form a complete understanding of the problem before trying to solve it. Thus, Pat's style is "burst-y"; first they read a lot, then they act on it in a batch of activity. [Sources: 7, 9, 18, 23, 25, 26, 29, 30, 31, 35, 37]
Attitude to Technology
Pat is generally comfortable using familiar technology, but they do not get a big kick out of obtaining the latest gadgets or learning how to use them f . Pat prefers to stay with the technologies for which they have already mastered the peculiarities [5, 28], because of the following facets:
- Computer Self-Efficacy g : : Pat has medium computer self-efficacy about doing unfamiliar computing tasks. If problems arise with their technology, Pat will keep on trying to figure out how to achieve what they have set out to do for quite awhile; Pat doesn't give up right away when computers or technology present a challenge to them. [Sources: 1, 2, 3, 4, 5, 6, 15, 17, 19, 22, 27, 28, 32, 34, 38]
- Attitude toward Risk h : Pat is busy and so they rarely have spare time. So Pat is risk averse and worries that they will spend time on their technology and not get any benefits from doing so. Pat prefers to perform tasks using familiar features, because they're more predictable about what Pat will get from them and how much time they'll take. [Sources: 10, 14, meta-analysis 12, survey 39]
- Learning: by Process vs. Tinkering i : When Pat sees a need to learn new technology, they do so by trying out new features or commands to see what they do and to understand how the software works. When Pat does this, they do so purposefully; that is, Pat reflects on each bit of feedback they get along the way to understand how the feature might benefit them. Eventually, if Pat doesn't think it will get them closer to what they want to achieve, Pat will revert back to ways that they already know will work. [Sources: 4, 5, 8, 11, 21, 36]
Tim (Timothy/Timara) Persona Foundations
Tim represents a fraction of people with backgrounds similar to theirs. For gender data on people similar to and different from Abi, see the Footnotes.
Note: All gray-background portions are fundamental to Tim. In contrast, the white-background portions can be customized to match your software's target audience.

- 28 years old
- Employed as an Accountant
- Lives in Cardiff, Wales
Tim loves public transportation. They know several routes to get there from home and they're always exploring ways to optimize their trips into the office. Work starts with email, which Tim answers one at a time, as soon as they read them a . (Sometimes this backfires, if there is a second related message Tim hasn't read yet, but Tim doesn't mind sending a follow-up email.) Some nights Tim plays computer games with their online friends. [Sources: 7, 9, 18, 23, 25, 26, 29, 30, 31, 35, 37]
Background Knowledge and Skills
- Tim works as an accountant. They just moved to this employer 1 week ago, and their software systems are new to Tim b . For Tim, technology is a source of fun, and they are always on the lookout for new computer software. Tim likes to make sure they have the latest version of all software with all the new features. [Sources: 40, 16, 33]
- Tim says they're a "numbers person" c , but Tim has not taken any computer programming or IT classes. Tim likes Math and knows how to think in terms of numbers c . Tim writes and edits spreadsheet formulas for their work. [Sources: 16, 33]
- Tim plays the latest video games, has the newest smart phone and a hybrid car. They download and install the latest software, and experiment with its settings. d Tim is comfortable and confident with technology and they enjoy learning about it and using new technologies. [Sources: 5, 6, 10, 20, 21, 24, 28, 37]
Motivations and Strategies
- Motivations d : Tim likes learning all the available functionality on all of their devices and computer systems they use, even when it may not be necessary to help Tim achieve their tasks. Tim sometimes finds themself exploring functions of one of their gadgets for so long that they lose sight of what they wanted to do with it to begin with. [Sources: 5, 6, 10, 20, 21, 24, 28, 37]
- Information Processing Style e : Tim leans towards a selective information processing style or "depth first" approach. That is, they usually delve into the first promising option, pursue it, and if it doesn't work out Tim backs out and gathers a bit more information until they see another option to try. Thus, Tim's style is very incremental. [Sources: 7, 9, 18, 23, 25, 26, 29, 30, 31, 35, 37]
Attitude to Technology
For Tim, technology is a source of fun, and they are always on the lookout for new computer software f . Tim likes to make sure to have the latest version of all software with all the new features [5, 28], because of the following facets:
- Computer Self-Efficacy: g Tim has high confidence in their abilities with technology, and thinks they're better than the average person at learning about new features. If they can't fix the problem, Tim blames it on the software vendor; it's not Tim's fault if he can't get it to work. [Sources: 1, 2, 3, 4, 5, 6, 15, 17, 19, 22, 27, 28, 32, 34, 38]
- Attitude toward Risk: h : Tim doesn't mind taking risks using features of technology that haven't been proven to work. When Tim is presented with challenges because they have tried a new way that doesn't work, it doesn't change their attitudes toward technology. [Sources: 10, 14, meta-analysis 12, survey 39]
- Learning: by Process vs. by Tinkering i : Whenever Tim uses new technology, they try to construct their own understanding of how the software works internally. Tim likes tinkering and exploring the menu items and functions of the software in order to build that understanding. Sometimes Tim plays with features too much, losing focus on what they set out to do originally, but this helps them gain better understanding of the software. [Sources: 4, 5, 8, 11, 21, 36]
Footnotes
a This is tied to information processing style e .
b GenderMag incorporates cognitive walkthroughs, and cognitive walkthroughs evaluate learnability by a new user [40].
c The stereotype of gender differences in mathematics performance has been debunked in recent years: controlling for stereotype threat shows no statistical gender differences in math performance [ 16]. To avoid evaluators inappropriately invoking that stereotype, we have made explicit that all four personas are good at math and enjoy math. The "numbers person" phrase is a verbatim quote from an interview with a woman accountant [33].
d Motivations: Research spanning over a decade has found that women tend (statistically) to be motivated to use technology for what it enables them to accomplish, men's motivations sometimes come
from their enjoyment of the technology for its own sake, and many people's motivations, no matter what their genders, are a mix. Differences in motivations can affect which features of problem-solving software different individuals choose to use. Sources: [5, 6,
10, 20, 21, 24, 28, 37].
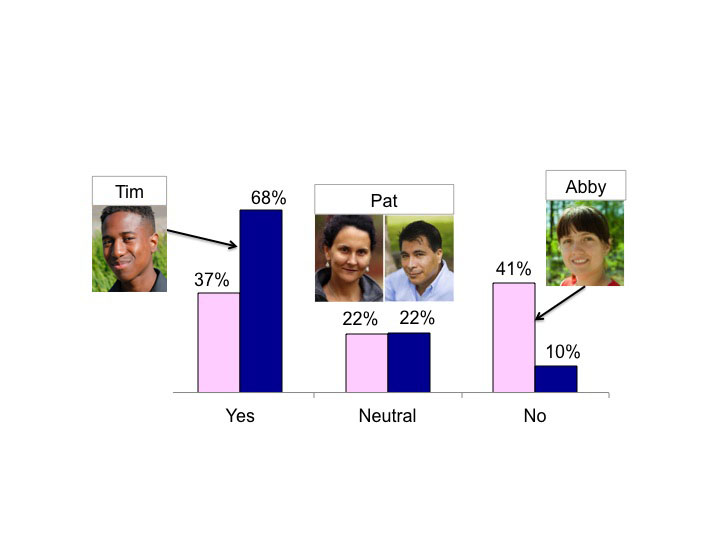
Sample data: Figure 1 shows data from a study (two genders represented) in [5], which is one portion of the foundations of the Motivations facet values. In that study, about 2/3 of men and 1/3 of women were
motivated by exploring next-generation technology, and this value for the Motivations facet is covered by Tim; about 1/5 of both men and women felt neutral about it (covered by the two Pats). The largest percentage of women and smallest
percentage of men did not enjoy exploring next-generation technology (covered by Abi).
e Information processing style: To solve problems, people often need to process new information, and there is extensive research reporting gender differences here too. In essence, when problem-solving, women are more statistically likely to use comprehensive information processing styles-gathering fairly complete information before proceeding-than other people. Men are more statistically likely than other people to use selective styles-following the first promising information, then potentially backtracking, in "depth first" order. But individually, anyone of any gender can have either of these styles or a mix of both. Each of these styles has particular advantages, but either is at a disadvantage when not supported by the problem-solving software environment. Particularly relevant here are studies tying gender differences in information processing style to software-based tasks, such as with e-commerce web sites, software-based auditing, and sensemaking in spreadsheets. Sources: [ 7, 9, 18, 23, 25, 26, 29, 30, 31, 35, 37].
f Sources: [5, 28]. This also ties back to Motivations d .
g Computer self-efficacy: One specific form of confidence is self-efficacy: a person's confidence about succeeding given a specific task. Self-efficacy matters to problem solving because a person's self-efficacy influences their use of cognitive strategies, amount of effort put forth, level of persistence, and strategies for coping with obstacles. Empirical data have shown that women tend statistically to have lower computer self-efficacy than other people, and men to have higher, as one would expect given phenomena like stereotype threat, and non-inclusive work environments and education practices. To date, we have been able to find self-efficacy data on only those two genders. Self-efficacy levels, in turn, affect people's behavior with technology, such as which features they choose to use and how willing they are to persist with hard-to-use features. Fortunately, features designed explicitly for diverse self-efficacy levels have been shown to be preferred by everyone. Sources: [1, 2, 3, 4, 5, 6, 15, 17, 19, 22, 27, 28, 32, 34, 38].
h Risk aversion: Studies have shown that women tend statistically to be more risk-averse than men [10], [14], surveyed in [39], and meta-analyzed in [12] -- in numerous decision-making domains, such as in ethical decisions, investment decisions, gambling decisions, health/safety decisions, career decisions, and others. In contrast, we have been unable to locate any study in any domain reporting men to be more risk-averse than women. Applying these findings on risk aversion to software usage suggests that risk aversion can impact women's decisions as to which feature sets to use. Reports are emerging on risk-aversion beyond those two genders, so we may be able to update this explanation soon. Sources: [10, 14, meta-analysis 12, survey 39]
i Tinkering: Research across age groups and professions reports women being statistically less likely to playfully experiment ("tinker") with features new to them, compared to men. However, when women do tinker, studies report that they are more likely to reflect more in the process and thereby sometimes profit from it more than men do. Further, some men tinker excessively. So far, data on this facet are available on only two genders. One effect of these differences in tinkering behaviors is their impact on which features of software women vs. men will elect to use, especially when a design choice underlying the software product is that users will learn new features by exploring and tinkering with them. Sources: [4, 5, 8, 11, 21, 36].
References
[1] Markus Appel, Nicole Kronberger and Joshua Aronson. 2011. Stereotype threat impairs ability building: Effects on test preparation among women in science and technology, European Journal of Social Psychology, 41(7), 904-913.
[2] Albert Bandura. 1986. Social Foundations of Thought and Action. Prentice Hall, Englewood Cliffs, NJ, USA.
[3] Laura Beckwith, Margaret Burnett, Susan Wiedenbeck, Curtis Cook, Shraddha Sorte, and Michelle Hasting. 2005. Effectiveness of end-user debugging software features: Are there gender issues? In Proceedings CHI, ACM, 869-878.
[4] Laura Beckwith, Cory Kissinger, Margaret Burnett, Susan Wiedenbeck, Joey Lawrance, Alan Blackwell, and Curtis Cook. 2006. Tinkering and gender in end-user programmers' debugging. In Proceedings CHI, ACM, 231-240.
[5] Margaret Burnett, Scott Fleming, Shamsi Iqbal, Gina Venolia, Vidya Rajaram, Umer Farooq, Valentina Grigoreanu, and Mary Czerwinski. 2010. Gender differences and programming environments: across programming populations. In Proceedings ACM Empirical Software Engineering and Measurement (ESEM), ACM.
[6] Margaret Burnett, Laura Beckwith, Susan Wiedenbeck, Scott Fleming, Jill Cao, Thomas Park, Valentina Grigoreanu, and Kyle Rector. 2011. Gender pluralism in problem-solving software. Interacting with Computers 23, 450-460.
[7] Patricia Cafferata and Alice Tybout. 1989. Gender Differences in Information Processing: A Selectivity Interpretation, Cognitive andAffective Responses to Advertising. Lexington Books.
[8] Jill Cao, Kyle Rector, Thomas Park, Scott Fleming, Margaret Burnett, and Susan Wiedenbeck. 2010a. A debugging perspective on end-user mashup programming. In Proceedings IEEE Visual Languages and Human-Centric Computing, IEEE, 149-156.
[9] Jill Cao, Irwin Kwan, Faezeh Bahmani, Margaret Burnett, Scott Fleming, Josh Jordahl, Amber Horvath, and Sherry Yang. 2013. End-user programmers in trouble: Can the Idea Garden help them to help themselves? In Proceedings Symposium on Visual Languages and Human-Centric Computing, IEEE.
[10] Justine Cassell. 2002. Genderizing HCI, In J. Jacko and A. Sears (eds), The Handbook of Human-Computer Interaction, Lawrence Erlbaum, 402-411.
[11] Shuo Chang, Vikas Kumar, Eric Gilbert, and Loren Terveen. 2009. Specialization, homophily, and gender in a social curation site: Findings from Pinterest. In Proceedings ACM Computer Supported Cooperative Work & Social Computing, ACM, 674-686.
[12] Gary Charness and Uri Gneezy. 2012. Strong Evidence for Gender Differences in Risk Taking. Journal of Economic Behavior & Organization 83, 1, (June 2012), 50-58.
[13] Constantinos Coursaris, Sarah Swierenga, and Ethan Watrall. 2008. An empirical investigation of color temperature and gender effects on web aesthetics. Journal of Usability Studies 3, 3, 103-117.
[14] Thomas Dohmen, Armin Falk, David Huffman, Uwe Sunde, Juergen Schupp and Gert G. Wagner. 2011. Individual risk attitudes: measurement, determinants, and behavioral consequences. Journal of the European Economic Association 9, 3, 522-550.
[15] Alan Durndell and Zsolt Haag. 2002. Computer self efficacy, computer anxiety, attitudes towards the Internet and reported experience with the Internet, by gender, in an East European sample. Computers in Human Behavior 18, 521-535.
[16] Nicole M. Else-Quest, Janet Shibley Hyde, Marcia C. Linn, 2010. Cross-national patterns of gender differences in mathematics: A meta-analysis, Psychological Bulletin 136(1), 103-127.
[17] Valentina Grigoreanu, Jill Cao, Todd Kulesza, Chris Bogart, Kyle Rector, Margaret Burnett, and Susan Wiedenbeck. 2008. Can feature design reduce the gender gap in end-user software development environments? In Proceedings Symposium on Visual Languages and Human-Centric Computing, IEEE, 149-156.
[18] Valentina Grigoreanu, Margaret Burnett, Susan Wiedenbeck, Jill Cao, Kyle Rector, and Irwin Kwan. 2012. End-user debugging strategies: A sensemaking perspective. Transactions on Computer-Human Interaction 19, 1, ACM.
[19] Kathleen Hartzel. 2003. How self-efficacy and gender issues affect software adoption and use. Communications ACM 46, ACM, 167-171.
[20] Jonas Hallstrom, Helene Elvstrand, and Kristina Hellberg. Gender and technology in free play in Swedish early childhood education. Int J. Technology and Design Education (2015), 25:137-149. DOI 10.1007/s10798-014-9274-z.
[21] Weimin Hou, Manpreet Kaur, Anita Komlodi, Wayne G. Lutters, Lee Boot, Shelia R. Cotten, Claudia Morrell, A. Ant Ozok, and Zeynep Tufekci. 2006. "Girls don't waste time": Pre-adolescent attitudes toward ICT. In Proceedings CHI Extended Abstracts, ACM, 875-880.
[22] Ann Hergatt Huffman, Jason Whetten, and William H. Huffman. 2013. Using technology in higher education: The influence of gender roles on technology self-efficacy. Computers in Human Behavior 29, 4, 1779-1786.
[23] William Jernigan, Amber Horvath, Michael Lee, Margaret Burnett, Taylor Cuilty, Sandeep Kuttal, Anicia Peters, Irwin Kwan, Faezeh Bahmani, and Amy Ko. 2015. A principled evaluation for a principled Idea Garden. In Proceedings of the 2015 IEEE Symposium on Visual Languages and Human-Centric Computing, October 2015. 8 pages.
[24] Caitlin Kelleher. 2009. Barriers to programming engagement. Advances in Gender and Education 1, 5-10.
[24a] Samantha Krieger, Mehgan Allen, & Catherine Rawn, (2015, February). Are females disinclined to tinker in computer science?. In Proceedings of the 46th ACM Technical Symposium on Computer Science Education (pp. 102-107).
[25] Michael Lee and Amy Ko. 2011. Personifying programming tool feedback improves novice programmers' learning. In Proceedings of the 7th International Workshop on Computing Education Research (ICER'11), 109-116. http://doi.acm.org/10.1145/2016911.2016934
[26] Michael Lee, Faezeh Bahmani, Irwin Kwan, Jilian Laferte, Polina Charters, Amber Horvath, Fanny Luor, Jill Cao, Catherine Law, Mihcael Bethwetherick, Sheridan Long, Margaret Burnett, and Amy Ko. 2014. Principles of a debugging-first puzzle game for computing education. In Proceedings of the 2014 IEEE Symposium on Visual Languages and Human-Centric Computing (VLHCC'14), 57-64.
[27] Ewa Luger. 2014. A design for life: Recognizing the gendered politics affecting product design, In CHI Workshop: Perspectives on Gender and Product Design. https://www.sites.google.com/site/technologydesignperspectives/papers
[28] Jane Margolis and Allan Fisher. 2003. Unlocking the Clubhouse: Women in Computing. MIT Press.
[29] Joan Meyers-Levy and Durairaj Maheswaran. 1991. Exploring differences in males' and females' processing strategies. Journal Consumer Research 18, 63-70.
[30] Joan Meyers-Levy and Barbara Loken. 2015. Revisiting gender differences: What we know and what lies ahead. Journal of Consumer Psychology 25, 1, 129-149.
[31] Ed O'Donnell and Eric N. Johnson. 2001. Gender effects on processing effort during analytical procedures. International Journal of Auditing 5, 91-105.
[32] Anne O'Leary-Kelly, Bill Hardgrave, Vicki McKinney, and Darryl Wilson. 2004. The influence of professional identification on the retention of women and racial minorities in the IT workforce. NSF ITWF & ITR/EWF Principal Investigator Conference, 65-69.
[33] Quote (verbatim): "I'm a numbers person." In interview with female accountant, age about 50, about working with spreadsheets. Interview conducted by Margaret Burnett, June 27, 2007.
[34] Piazza Blog. 2015. STEM Confidence Gap. http://blog.piazza.com/stem-confidence-gap/
[35] Rene Riedl, Marco Hubert, and Peter Kenning. 2010. Are there neural gender differences in online trust? An fMRI study on the perceived trustworthiness of ebay offers. MIS Quarterly 34, 2, 397-428.
[36] Daniela Rosner and Jonathan Bean. 2009. Learning from IKEA hacking: I'm not one to decoupage a tabletop and call it a day. In Proceedings CHI, ACM, 419-422.
[37] Steven John Simon. 2001. The impact of culture and gender on web sites: An empirical study. The Data Base for Advances in Information Systems 32, 1, 18-37.
[38] Anil Singh, Vikram Bhadauria, Anurag Jain, and Anil Gurung. 2013. Role of gender, self-efficacy, anxiety and testing formats in learning spreadsheets. Computers in Human Behavior 29, 3, 739-746.
[39] Elke Weber, Ann-Renee Blais, and Nancy Betz. 2002. A domain-specific risk-attitude scale: Measuring risk perceptions and risk behaviors. Journal Behavior and Decision Making 15, 263-290.
[40] Cathleen Wharton, John Rieman, Clayton Lewis, and Peter Polson. 1994. The Cognitive Walkthrough method: A practitioner's guide. In J. Nielsen and R. L. Mack (Eds.) Usability Inspection Methods, John Wiley, New York. (Also available as Technical Report #CU-ICS-93-07, University of Colorado, Institute of Cognitive Science, at http://ics.colorado.edu/techpubs/pdf/93-07.pdf).
Date of last update: Oct. 26, 2020
